Dear WordPress Administrators,
Fake CVE Phishing Alert! We hope this message finds you well. I’d like to bring your attention to a critical issue that could impact the security of your WordPress website.
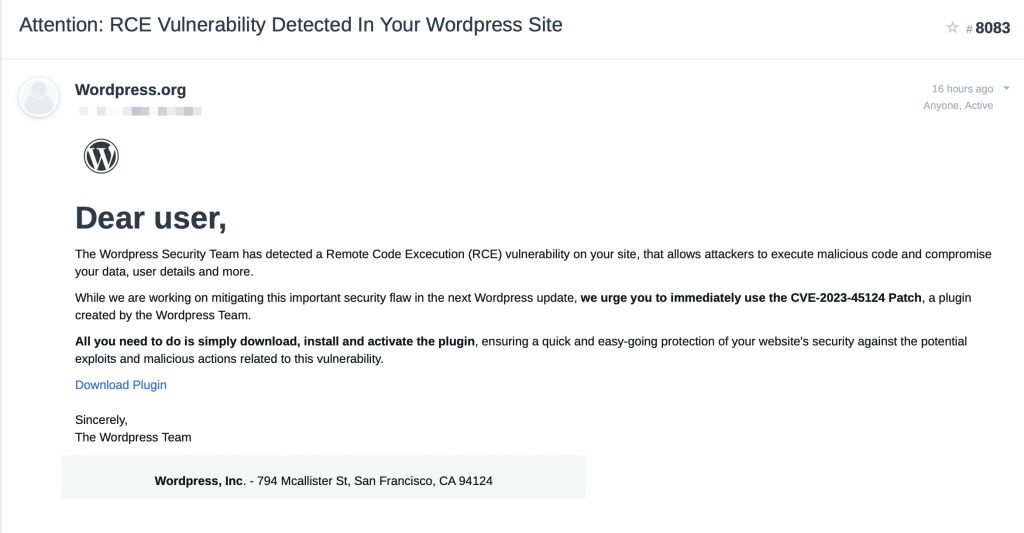
The Threat: Fake CVE-2023-45124 Phishing Campaign
Wordfence and PatchStack have recently unearthed a phishing campaign targeting WordPress administrators. This deceptive scheme involves sending fake security warnings, claiming to address a non-existent vulnerability named “CVE-2023-45124.” The malicious actors behind this campaign are duping unsuspecting victims into downloading a plugin that, instead of resolving a critical remote code execution (RCE) flaw, injects their sites with a harmful payload.
How It Works: A Sneaky Setup
The phishing campaign kicks off when an unsuspecting user clicks on the ‘Download Plugin’ button in a misleading email. This action directs the victim to a fake landing page cleverly designed to imitate the legitimate ‘wordpress.com.’ The page even displays fabricated user reviews to add an air of authenticity. Once the plugin is installed, it initiates a chain of malicious activities, including downloading a backdoor payload, establishing a hidden admin account, and transmitting the victim’s data to the attacker’s Command and Control (C2) Infrastructure.
The Dangers Lurking Within: Backdoor Features
The backdoor payload comes equipped with a range of dangerous features, allowing the attacker to take control of files, manipulate the server environment, and access sensitive information. This includes a SQL client, a PHP console, a command line terminal, and the ability to gather comprehensive details about the server environment. It poses a serious threat to the security and integrity of your WordPress site.
Protect Yourself: Recommendations from Andro Media
To safeguard your WordPress site, we strongly advise administrators to exercise caution when encountering any suspicious emails. Refrain from clicking on any links, including the Unsubscribe link, and avoid installing unfamiliar plugins on your website.
If, by any chance, you have fallen victim to this phishing campaign, take immediate action. Conduct a manual search on your site’s root directory to identify and remove the malicious plugin.
Stay Informed: Check Our Sources
For more details on this alarming issue, we encourage you to explore the following sources:
Your security is our top priority, and Andro Media is committed to keeping you informed and protected. If you have any concerns or need further assistance, please don’t hesitate to reach out.
Stay vigilant, stay secure.
Best regards,
Andro Media – Your SEO Partner
